ChatGPT and the Evolution of Data Interaction - A Double-Edged Sword
In the current age, where information zips through the digital landscape at unprecedented speeds, tools such as ChatGPT have revolutionized our engagement with data. These breakthroughs offer remarkable opportunities for enhancing efficiency and connection. However, they simultaneously heighten our vulnerability to potential hazards if data management isn't approached judiciously. Recognizing the limits of data exchange has become essential to safeguarding both individual and business security within the online environment.
Understanding Prohibited Data
What Constitutes Prohibited Data in Digital Communication?
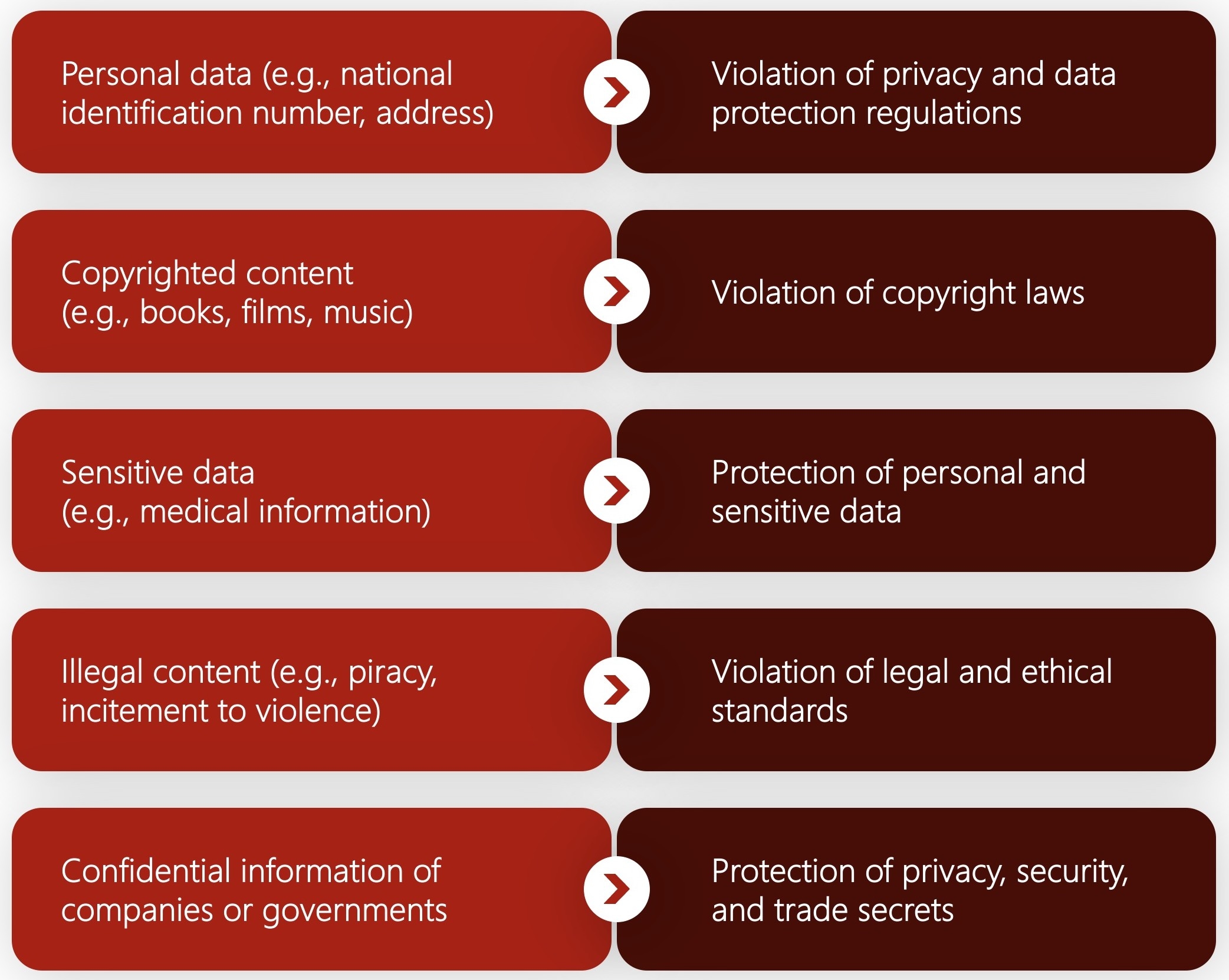
Prohibited data, often including personal identifiers and sensitive personal information, is data that, when disclosed, can compromise privacy and security. From social security numbers to private health details, understanding what constitutes prohibited data is the first step in safeguarding one's digital identity.
Personal Data and Privacy - Navigating the Digital Minefield
The sanctity of personal data is enshrined in numerous privacy laws across the globe. Yet, every day, individuals risk data exposure through digital platforms. Being aware of privacy policies and the specifics of data classified as 'personal' is not just a best practice—it's a necessity for digital survival.
Categories of prohibited information and their legal implications: