The omnipresence of the internet in our daily lives has brought immense convenience and a world of information at our fingertips. However, it has also ushered in new forms of vulnerabilities, notably in the realm of website security.
Comprehending the Fundamentals of Website Security
At its core, website security encompasses all measures implemented to guard against cyberattacks, aiming to protect both the website and the data it handles. It is an ongoing process, integral to website management. The challenges are perpetually evolving, as cybercriminals continually innovate, requiring website owners to stay abreast of the latest threats and countermeasures.
Exploring Various Types of Cyberattacks
A cyberattack is essentially an unauthorized intervention in the digital space. The implications can be dire, ranging from financial losses, data theft, to damage to reputation. For hackers, the most appealing targets are networks with lax security and users with limited awareness.

Various methods are employed by cybercriminals, such as:
- 1. Malware: These are malicious programs crafted to harm or exploit any device, application, or network. The impacts can be varied, from slowing down devices to extracting sensitive information. Brute force attacks, a subset of this category, primarily target weak passwords.
- 2. Advanced Techniques: Aside from malware, attackers employ advanced methods such as:
- - DoS and DDoS Attacks: These aim to overwhelm a website or network with a flood of traffic.
- - SQL Injection: This targets the databases of websites, aiming to manipulate or extract data.
- - Cross-Site Scripting (XSS): Here, attackers inject malicious scripts into websites, affecting users who visit these sites.
- - Phishing: It's a deceptive technique to trick users into revealing personal or financial details.
- - Ransomware: Here, cybercriminals encrypt a user's data, demanding a ransom for its release.
- - Defacement: Aiming to alter the visual appearance of a website, often to promote a particular message or cause.
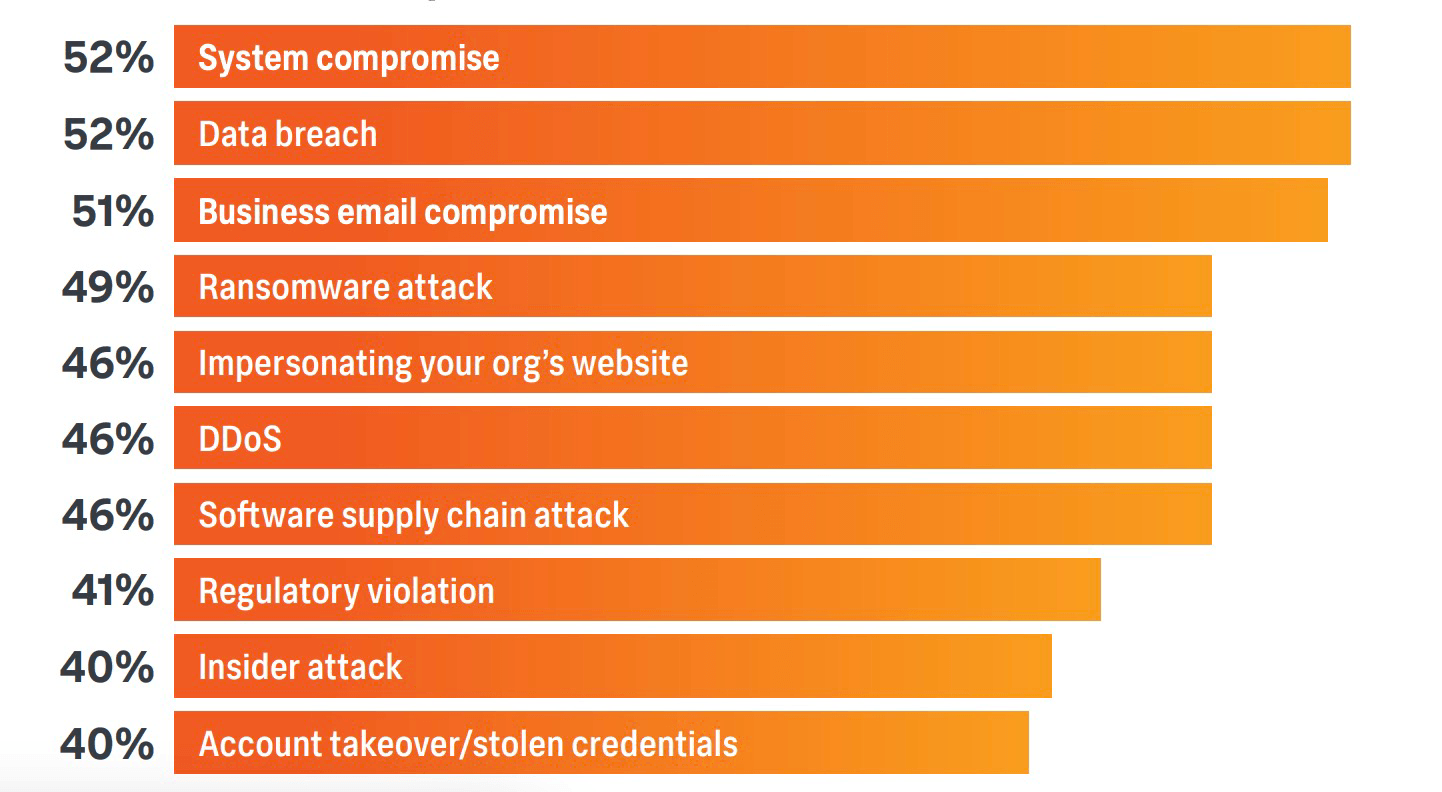
Reasons Behind Websites Being Targeted by Cybercriminals
Contrary to popular belief, it's not just high-profile websites that are at risk. Small, seemingly inconsequential sites can also be lucrative targets. Motivations can range from extracting sensitive data, leveraging server power for activities like crypto-mining, gaining notoriety in the hacking community, or merely pointing out software vulnerabilities.
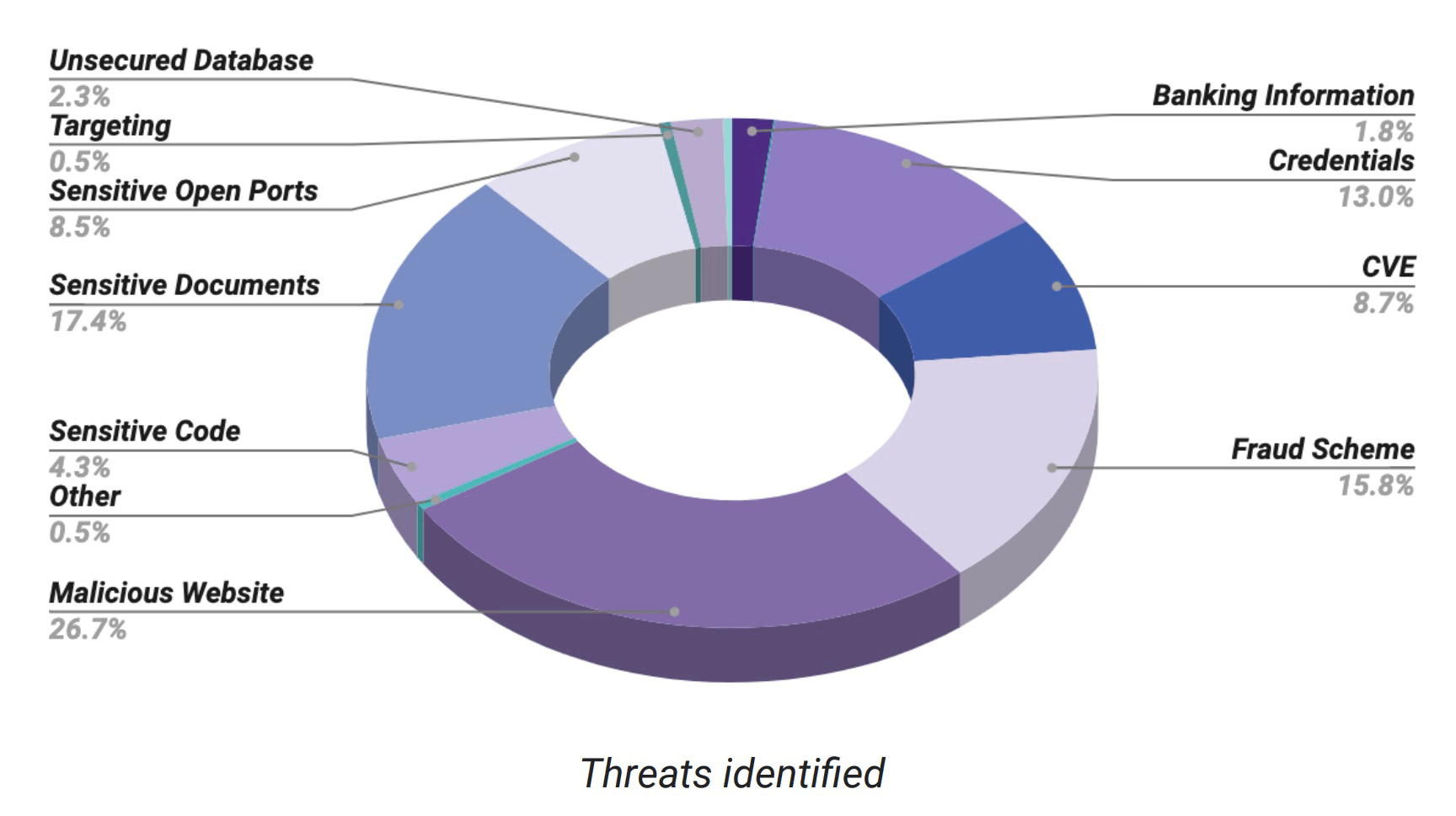
Significance of GDPR Compliance in Data Protection
The General Data Protection Regulation (GDPR) has reshaped the way data is collected and processed. It is essential for website operators to understand and adhere to these regulations. They mandate transparency, purpose limitation, data minimization, accuracy, retention limitation, and ensuring data integrity and confidentiality. Non-compliance can lead to hefty penalties, making it imperative for website owners to ensure adherence, especially in the wake of a data breach.
TYPO3: Leading the Way in CMS Security
In the contemporary digital landscape, a focus on security is not just a luxury but an absolute necessity. TYPO3, a leading Content Management System (CMS), places paramount importance on this principle.
TYPO3's Active Approach to Enhancing Security
- 1. Advanced Security Features: TYPO3 is equipped with state-of-the-art security tools. Encryption ensures data integrity, and authentication tools protect unauthorized access, making it a robust platform for website development.
- 2. Dedicated Security Team: One of TYPO3's standout features is its dedicated security team, tasked with addressing critical security challenges within the TYPO3 ecosystem. This team's roles include:
- - Rapidly addressing reported security issues concerning TYPO3 core and extensions.
- - Orchestrating the release of security patches.
- - Assisting developers in rectifying security problems.
- - Framing and disseminating TYPO3 security guidelines to the community.
- 3. Regular Security Updates: The TYPO3 team regularly rolls out security updates, ensuring that the CMS is equipped to handle the latest threats. Regular patching and updates are vital in the ever-evolving landscape of cybersecurity.
- 4. Community Engagement: TYPO3’s security isn't just about the dedicated team or the system's creators. The entire TYPO3 community actively participates in identifying vulnerabilities, sharing best practices, and continually improving the platform's security aspects.
Summary: How to effectively secure a website?
In the intricately woven fabric of today's digital age, the essence of security stands paramount. At FNX Group, we pride ourselves on being experts in cybersecurity, with a specialized focus on TYPO3 — a leading CMS that places security at the forefront of its offerings. The value of understanding myriad cyber threats, proactively implementing preventive measures, and choosing steadfast platforms like TYPO3 is immeasurable. It's not just about selecting a secure foundation but ensuring that the commitment to safety is ongoing. Continuously updating software, staying abreast of the latest threats, and imbibing a culture of unyielding security are quintessential. Together, these actions ensure that your digital assets not only remain safeguarded but also flourish in our increasingly digital world.